Lnk files can be used to help find what recent files a user was interacting with at a point in time. This is helpful in the event where you may suspect a user executed malicious macros that were embedded in a Microsoft Office document. When these types of events do occur, sometimes SIEM events can be ambiguous and lack context. There are a few different methods you use to hone in on what files the user was interacting with at the time the event occurred. One of the most helpfully locations I've found on disk in a user's profile are their Recent links.
This folder is a collection of shortcut links that the user has recently visited. By looking at the contents of the .lnk files, you can see where the documents the user was interacting with reside on the disk. You can use the time stamps on the actual file (not the .lnk file) to assist in correlating an event you're investigating. Keep in mind that the sooner you can check these from the time the event occurred, the more reliable they are. As time passes, and the user interacts with more and more files, the timestamps become less reliable.
Yes, they can be modified by malware or anything/one running in the user's context or higher; so, that's something to take into consideration.
The .lnk files are located in the following directory:
%userprofile%\AppData\Roaming\Microsoft\Windows\Roaming\Recent
I wrote the following script to help parse these files when I'm conducting analysis on endpoints. This usually helps when trying to build context off of an alert; "painting a picture of what happened" if you will...
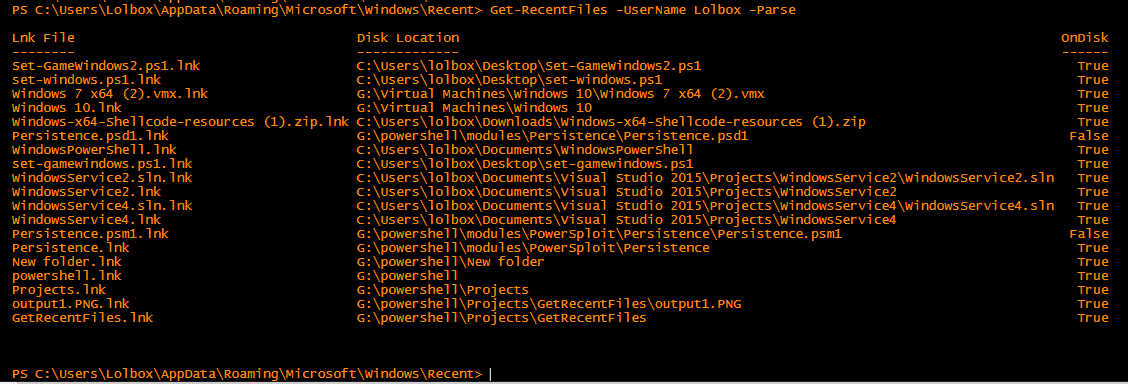
When ran without the -Parse argument, a list sorted by the LastWriteTime property is outputted for the username parameter that was passed to the username argument.
When ran with the -Parse option each file in the user's Recent directory will be parsed and a test will be ran to determine whether the file still exists or not
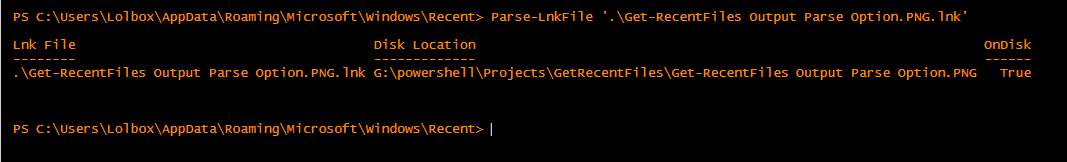
And lastly, you can parse individual Lnk files by simply running Parse-LnkFile <filename>. This is the function that within the Cmdlet that performs the parsing.
And below is the Git Gist. Happy hunting!